The Windows Registry
Please look at the article Inside the Registry by Russinovich.
From WFA, page 158:
"To most administrators and forensic analysts, the Registry probably looks like the entrance
to a dark, forbidding cave on the landscape of the Windows operating system. Others might see the Registry as a dark door
at the end of a long hallway, with the words "abandon hope, all ye who enter here" scrawled on it. The truth is that the Registry is a veritable gold mine of information for both the administrator and the forensics investigator."
Why? Well, one reason is that Windows is not tidy with respect to the Registry. Some information found in the Registry is old and even inconsistent, but that might sometimes provide us useful (if potentially confusing) historical information.
The Anatomy of the Window Registry
The Wikipedia article
Windows Registry and WF on page 129 list these system registry files and associated hives::
- %WINDIR%\System32\Config\Sam → HKEY_LOCAL_MACHINE\SAM
- %WINDIR%\System32\Config\Security → HKEY_LOCAL_MACHINE\SECURITY
- %WINDIR%\System32\Config\Software → HKEY_LOCAL_MACHINE\SOFTWARE
(and also Software\Wow6432Node for 32 bit apps on 64bit machines)
- %WINDIR%\System32\Config\System → HKEY_LOCAL_MACHINE\SYSTEM
- %WINDIR%\System32\Config\Default → HKEY_USERS\.DEFAULT
The Anatomy of the Registry
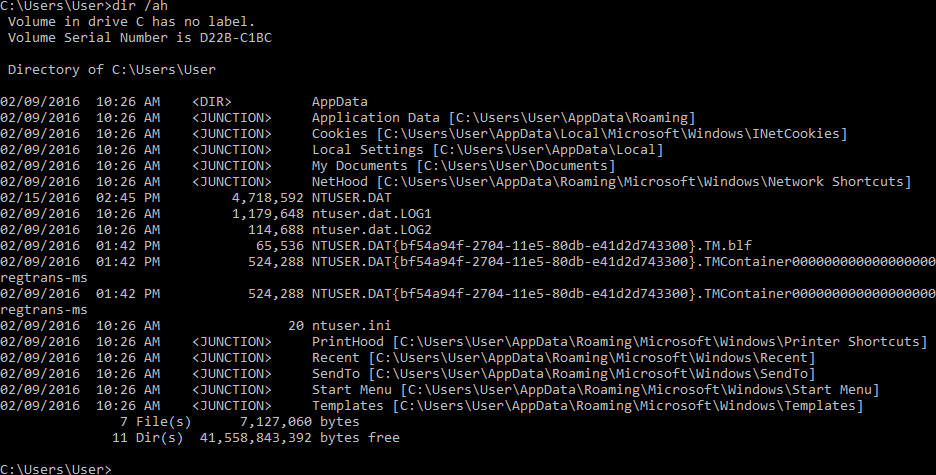
On a per-user basis, you can find the user profile "NTUSER.DAT" file in different locations:
- Windows 2008, Vista, Windows 7, Windows 8, Windows 10: %USERPROFILE%\NTUSER.DAT → HKEY_USERS\user (Note this is a "hidden" file, so you will need to use the dir /ah flag)
- XP, 2003, 2000: DOCUMENTS AND SETTINGS → HKEY_USERS\user
NTUSER.DAT
The Anatomy of the Registry
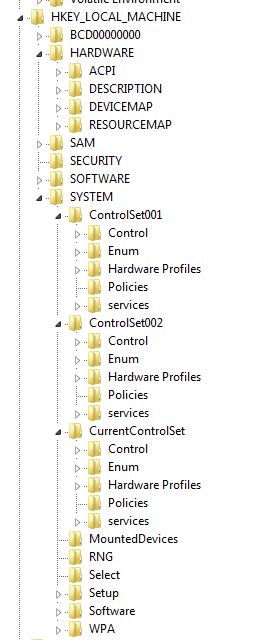
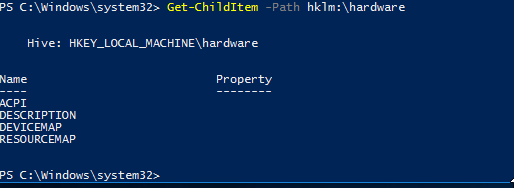
There are also "volatile" hives created on-the-fly, which you will only be to examine from a live machine or an image of a live machine:
- HKEY_LOCAL_MACHINE\Hardware
Via powershell
Via powershell
The Guts of the Registry
Each registry entry is a key-value pair. The data types supported for values are
- REG_BINARY — binary data
- REG_DWORD — 4 byte integers
- REG_SZ — fixed-length strings
- REG_EXPAND_SZ — variable length strings
- REG_MULTI_SZ — multiple strings separated by a delimiter
- REG_NONE — no data type
- REG_QWORD — 8 byte integers
- REG_LINK — a symbolic link
- REG_RESOURCE_LIST — a list of resources
- REG_RESOURCE_REQUIREMENTS_LIST — a list of possible hardware resources for a device driver
- REG_FULL_RESOURCE_DESCRIPTOR — a list of resources for a hardware device
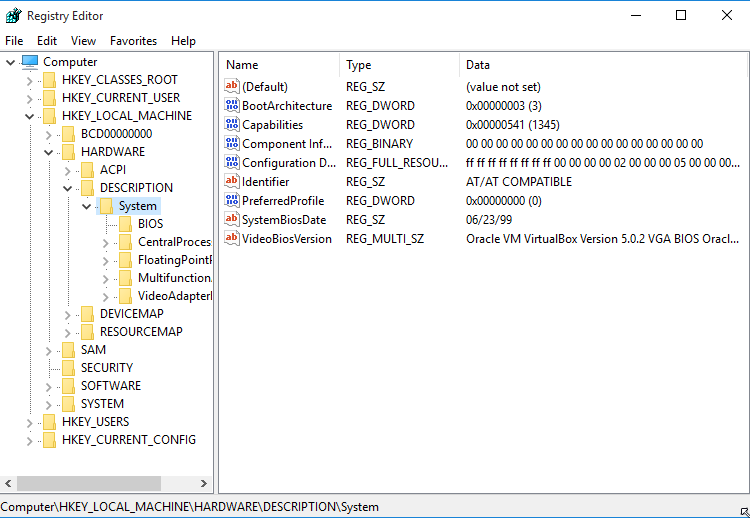
Registry via regedit example
Looking at the raw registry
WF goes into quite a bit of detail on pages 130-135 about how the registry is physically constructed. The important items to take away from this are:
- A hive is made up of cells: key, value, subkey list, value list, and security descriptor cells.
- Each of these has a signature that might be useful for looking at raw dumps, where we might find
these, either from older versions that might have been deleted, or copies made explicitly.
- The program chntpw is also useful as a raw registry editor — and it's even in your Synaptic repository so go ahead and install it.
- Each key cell has a time value called "LastWrite" time. This temporal information can be used for forensic purposes, such as creating a timeline for a system.
-
Spotting changes
Sysinternals Regmon has been superseded by "Process Monitor". It might prove useful when watching a system, but the registry information is copious and not as easy to filter as one would like.
What all can we try to extract?
System information:
- The computer name
- Last shutdown time
- Product name and service pack
- Installation date
What all can we try to extract?
Timezone: It's critical to note that logs generally show local time, but system activities are generally done in UTC.
What all can we try to extract?
Shares:
- Shares aren't just remote partitions.
- Administrative shares, which include IPC shares
- However, these activities can be suppressed by a system administrator, so don't always expect to find them.
What all can we try to extract?
Audit policy: what do we expect to find in the logs?
- System events
- Logon events
- Object access
- Privilege use
- Process tracking
- Policy changes
- Account management
- Directory service access
- Account logon events
-
What all can we try to extract?
Wireless SSIDs: yes, even wireless SSIDs can be stored in
..\Microsoft\WZCSVC\Parameters\Interfaces\
What all can we try to extract?
Autostart locations: these are one of the favorite places for malware to obscure autostartup processes.
- System boot: \HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
- User Login; generally, in a normal boot, at least 1,3,5,6 will be executed:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Runonce
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows NT\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
What all can we try to extract?
User Activity:
- HKEY_LOCAL_MACHINE\Software\Classes\Exefile\Shell\Open\command
- HKEY_CLASSES_ROOT\Exefile\Shell\Open\Command
- HKEY_CLASSES_ROOT\Word.Document.x\shell\open\command
- HKEY_LOCAL_MACHINE\Software\Microsft\Command Processor\Autorun
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs (obscure and effective)
What all can we try to extract?
USB removable storage:
What all can we try to extract?
Mounted devices:
- HKEY_LOCAL_MACHINE\System\MountedDevices
- Remember, mounted devices in the Windows world are going to often share drive identifiers.
- Also, don't forget that one physical device can show up as multiple logical drives, such as U3 devices.
- Trying to match physical devices to forensic traces on a system unfortunately is not as simple as it could be. While some information is maintained in the registry, it's not conclusive by any means. Try to get information about manufacturer, any GUIDs you can find, serial numbers, and device class IDs.
- Also, look at individual user's NTUSER.DAT files for sub-keys to Software\Microsoft\Windows\CurrentVerions\Explorer\MountsPoints2
The registry and users
- Windows doesn't facilitate direct access into its registry with respect to user information.
- The WF DVD includes a ProScript "UserDump.pl" that can be used with ProDiscover.
- With it, you can extract some information: account creation, last login, account expiration, and last failed login.
- Even more usefully, though, you can use the Perl Win32::TieRegistry module and the Win32API::Registry module (the WF book suggests using the Parse::Win32Registry module, but that has now been superseded by these two modules) to extract user information from an image or even live.
- Most of the usable logging information is in the hive HKEY_CURRENT_USER.
- Look at Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count
- Incredibly, these keys are encoded with the old, incredibly hacky ROT-13 cipher. In them, you can find the absolute path name of binaries executed, how many times they were executed, and when the last execution occurred. Thanks, Microsoft!
Recent Documents
- Windows also maintains "MRU" (most recently used) lists that can be useful.
- \Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
- \Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
- \Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU
- \Software\Microsoft\Search Assistant\ACMru
- Also, Windows keeps a TypedURLs key at \Software\Microsoft\Internet Explorer\TypedURLs
Network Drives
You can also look at Software\Microsoft\Windows\CurrentVersion\Explorer\Map Network Drive MRU and
Software\Microsft\Windows\CurrentVersion\MountPoints2 to see what network drives have been mapped. You can alsofind IP addresses in Softare\Microsfot\Windows\CurrentVersion\Explorer\ComputerDescriptions.
P2P and IM
These are popular (and prominently used for malware propagation); it's certainly worth looking at the registry to see what you can see, but every program is going to use different keys and standards for values.
Restore Points
The most important keys to remembering about Windows restore points (1) they don't always get made, so not having current restore points is not necessarily due to malicious behavior (2) installation of software (even malware) can trigger the creation of a new restore point, a very handy feature for finding what might have been installed recently.






